⚠️Safety Tips
Revoking Contract Permissions
Introduction
In the world of decentralized finance (DeFi) and blockchain transactions, security is paramount. One crucial aspect of maintaining security is the management of smart contract permissions. When you interact with a decentralized application (dApp) or smart contract, you often grant it permission to access your tokens. These permissions, if left unchecked, can pose significant security risks.
Why is Revoking Permissions Important?
Persistent Access: Many dApps and smart contracts require permissions to interact with your tokens. However, these permissions often do not expire on their own, granting the dApp continuous access to your assets.
Security Risks: This indefinite access can be exploited. If a dApp you’ve interacted with is compromised, or if it was malicious from the start, your tokens can be at risk.
Prevention of Unauthorized Transactions: By revoking permissions, you ensure that no unwanted or unauthorized transactions can be made by these contracts, safeguarding your digital assets.
Good Security Practice: Regularly reviewing and revoking permissions is akin to changing passwords regularly in traditional online security - it's a fundamental practice for digital safety.
Revoke.cash: Your Tool for Enhanced Security
Revoke.cash is a user-friendly platform designed to enhance your security in the DeFi space by allowing you to easily revoke permissions granted to smart contracts.
Features of Revoke.cash:
Comprehensive Overview: revoke.cash displays all the permissions you have granted to different smart contracts, giving you a complete picture of your exposure.
Support for Multiple Networks: Initially focused on Ethereum, revoke.cash now supports various blockchain networks, catering to a wide range of users.
Simple and Intuitive: The platform offers an easy-to-navigate interface, making it accessible even to those new to DeFi.
Free to Use: Revoke.cash is a free tool, emphasizing the importance of security for all users in the blockchain ecosystem.
How to Use Revoke.cash:
Connect your wallet to the platform.
Review the list of contracts that have access to your tokens.
Select the permissions you wish to revoke.
Confirm the transaction to revoke these permissions.
Alternative: Rabby Wallet
Rabby Wallet is more than just a cryptocurrency wallet; it's a powerful tool designed to simplify and secure your interactions within the DeFi ecosystem. One of its standout features is the built-in functionality to manage and revoke smart contract permissions.
Key Features of Rabby Wallet for Permission Management:
Integrated Permission Manager: Rabby Wallet includes a dedicated section named "Approvals" for permission management. This integration allows users to easily review and manage the permissions they have granted to various smart contracts and dApps, all within the wallet interface.
One-Click Revocation: With Rabby Wallet, revoking permissions is as simple as a single click. This ease of use encourages regular review and revocation of permissions, enhancing your overall security.
Enhanced Security: By consolidating the management of your digital assets and their permissions in one place, Rabby Wallet significantly reduces the risk of unauthorized access and transactions.
Customizable Settings: Users can tailor their experience by setting preferences for how they manage and revoke permissions, making it a flexible tool that adapts to individual security needs.
Using Rabby Wallet for Permission Management:
Open your Rabby Wallet and navigate to the "Approvals" section.
Review the list of smart contracts with access to your tokens.
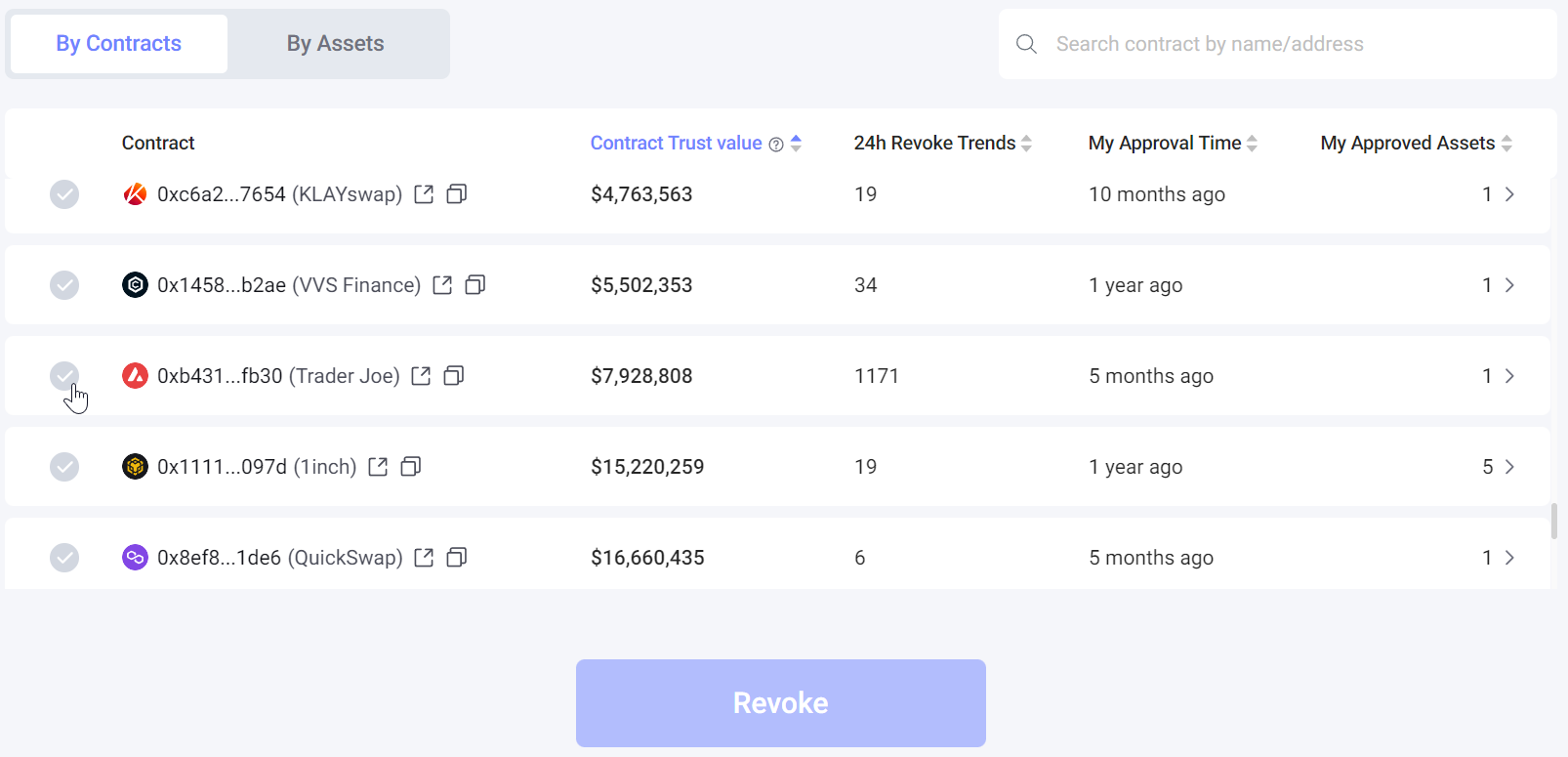
Identify any permissions that are no longer needed or pose a potential security risk.
Use the one-click feature to revoke these permissions instantly, and sign on the wallet.
Confirm the transaction to revoke these permissions.
Regularly check this section to stay on top of your permission settings.
Check Your Wallet Extension
Protect Your Assets from Fake Chrome Wallet Extensions
Introduction
As the crypto ecosystem grows, so does the sophistication of attacks targeting everyday users. A major emerging threat involves malicious clones of popular browser wallet extensions, distributed through phishing links, compromised sites, or third-party app stores.
In March 2025, Microsoft reported the discovery of a new trojan named "StilachiRAT", designed to target browser-based cryptocurrency wallets on Google Chrome, capturing sensitive information like private keys, seed phrases, and session data.
This threat highlights a crucial aspect of wallet security: verifying the legitimacy of your browser wallet extension.
Why It Matters
When you install a wallet extension like MetaMask or Trust Wallet on your browser, it is identified by a unique Extension ID, similar to a digital fingerprint. Attackers often distribute fake versions of these extensions under different IDs — even though they may visually appear identical.
By comparing the Extension ID of your installed wallet with the official ID published by the wallet developers or security platforms, you can verify its authenticity and prevent potential compromise.
How to Check Your Wallet Extension on Chrome
Follow these steps to verify the extension installed in your browser:
Open Chrome and go to the address bar. Type:
chrome://extensionsand press Enter.Enable Developer Mode using the toggle switch in the top-right corner of the page.
Find the wallet extension you want to verify (e.g., MetaMask, Trust Wallet).
Click the “Details” button.
In the URL section, look at the Extension ID. This is a 32-character string.
Compare the Extension ID with the list of official IDs below. If your ID does not match, uninstall the extension immediately and scan your system for malware.
Official Wallet Extension IDs
Rabby
acmacodkjbdgmoleebolmdjonilkdbch
MetaMask
nkbihfbeogaeaoehlefnkodbefgpgknn
Trust Wallet
egjidjbpglichdcondbcbdnbeeppgdph
Coinbase Wallet
hnfanknocfeofbddgcijnmhnfnkdnaad
Bitget Wallet
jiidiaalihmmhddjgbnbgdfflelocpak
TronLink
ibnejdfjmmkpcnlpebklmnkoeoihofec
TokenPocket
mfgccjchihfkkindfpnnaooecgfneiiil
OKX Wallet
mcohilncbfahbmgdjkbpemcciiolgcge
BNB Chain Wallet
fhbohimaelbohpjbbldcngcnapndodjp
Keplr
dmkamcknogkgcdfhhbddcghachkejeap
Phantom
bfnaelmomeimhlpmgjnjophhpkkoljpa
Braavos (Starknet)
jnlgamecbpbmajjfhmnmleljkemedjdma
Leap Cosmos Wallet
fcfclflflndlomdbehhjjcoimbgofdncg
Sui Wallet
opcgpfmipidbgpenhmajoajpbobppdil
Manta Wallet
enabgbdfcbaehmbigakjijjabdcpdnimlg
Compass Wallet (Sei)
anokgpmhncpekklhclmimgpjmncooiifb
Math Wallet
afbcjbppbfadlkmhmclhlkeedmamcflc
Fractal Wallet
cekghljhjkibikfgllpfffbfeeeggkddd
Station Wallet
aiifbnfobpmeekiipeheeiijndpnlgpgp
ConfluxPortal
bijibmknhoneiaglclpifcccjkochdkoh
Plug
cfbdfhimifmdmehjdnkobpcjfeffblkjm
This list is based on verified data as of March 2025. Always cross-reference with the official wallet websites for the most up-to-date information.
Additional Best Practices
To further reduce the risk of compromise and maintain a secure crypto environment, users should:
Avoid installing browser extensions from unofficial sources or third-party websites. Always download from the official Chrome Web Store link provided on the wallet's website.
Never store or copy-paste your private key or seed phrase into a browser or external document. Use only hardware wallets or secure, encrypted storage methods when necessary.
Beware of unsolicited prompts, or website overlays that ask you to re-enter your seed phrase, approve unknown transactions, or download “updates.”
Enable browser-level security features such as real-time phishing protection, and keep your Chrome browser up-to-date.
Conclusion
Verifying the authenticity of your wallet browser extension is a fundamental and often overlooked layer of security. With malware like StilachiRAT actively targeting users through fake Chrome extensions, due diligence is more critical than ever.
Stay informed, stay cautious, and always verify before you trust.
Hot vs. Cold Wallets: Securing Your Assets
Hot Wallets: Understanding the Risks
Hot crypto wallets are connected to the internet. They offer a series of features, from storing, sending, and receiving tokens to managing and viewing all available tokens in one place. Hot wallets are accessible from internet-enabled devices such as cellular phones, tablets, and laptops.
However, this constant internet connectivity also introduces risks. They are more susceptible to online threats like hacking, phishing attacks, and malware. Users must be vigilant about their device security and cautious of online vulnerabilities to protect their assets in hot wallets.
Online Vulnerabilities: Susceptible to cyber threats like hacking and phishing.
Device Security Dependence: The wallet's safety is directly tied to the security of your device.
Software Risks: Potential vulnerabilities in wallet software.
Third-party Risks: Exposure to risks associated with the host platform.
Phishing Attacks: High risk of phishing schemes targeting wallet users.
Keylogging and Screen Capture Malware: Risk of malicious software capturing wallet credentials.
Connection Interception: Danger of data interception, especially over unsecured networks.
Cold Wallets: Enhanced Security
Cold wallets, unlike their hot counterparts, are not connected to the internet. This absence of internet connectivity significantly lowers their vulnerability to hacking and online threats. The increased security offered by cold wallets has led to their growing popularity, especially in the wake of incidents like the FTX collapse in November 2022, where many users lost access to their digital assets due to bankruptcy and alleged hacking.
Typically resembling USB sticks, these hardware devices, along with paper wallets, represent forms of cold storage and generally cost between $50 to $200. The heightened security of cold wallets is largely attributed to their offline storage of private keys, which are essential for executing transactions, contrasting with the online storage of keys in hot wallets.
Superior Security: Cold wallets store private keys offline, protecting against online threats.
Physical Transaction Confirmation: For transactions made using a hot wallet linked to a Ledger, each transaction requires physical confirmation on the Ledger device. This means you must physically click a button on the Ledger to confirm any transaction initiated, adding an extra layer of security against unauthorized transactions.
Full Control Over Assets: Direct control over your crypto, without third-party reliance.
Long-Term Safe Storage: Ideal for storing substantial crypto amounts securely.
Physical Security: Physical possession required for access, ensuring security.
Using a Cold Wallet like Ledger not only provides superior protection for your assets but also ensures that each transaction is explicitly authorized, safeguarding against unwanted or malicious transactions.
In conclusion, while hot wallets offer convenience and are suitable for exploring and testing DeFi protocols with smaller amounts (around $200), they are not ideal for holding larger assets due to the inherent online risks. For securing significant amounts, cold wallets are distinctly superior.
They provide robust security against online threats, ensure physical transaction confirmations, and offer complete control over your assets. For substantial investments and long-term storage, opting for a cold wallet like Ledger is a prudent choice to ensure the utmost safety and control over your digital assets.
Secure your SPACE with Ledger for the utmost safety and control over your digital assets.
Guide to Safe Airdrop Farming
Introduction
The allure of airdrop farming in the crypto world is undeniable, but it's fraught with risks ranging from phishing scams to Sybil attacks. Awareness and caution are paramount for anyone venturing into this area.
Expanded Risks of Airdrop Farming
Phishing Scams: These scams are particularly insidious. Perpetrators create fake websites or communication channels mimicking legitimate airdrops. They often request sensitive information, leading to the loss of tokens or control over wallets.
Malicious Smart Contracts: Some airdrops require you to interact with smart contracts that could be programmed with hidden malicious functions. These functions might enable unauthorized access to your funds or personal data.
Sybil Attacks: In a Sybil attack, attackers create numerous fake identities to flood and manipulate a network, often targeting airdrop participants to gain undue advantage or disrupt normal operations.
Enhanced Best Practices for Airdrop Safety
1. Separate Device or Browser Profile
Using a separate device or a distinct browser profile for airdrop farming isolates your regular browsing and financial activities from potential threats associated with airdrops.
2. Regular Browser Data Clearance
Regularly clearing your browser’s cache and history prevents the accumulation of tracking cookies and malicious scripts that could compromise your online security.
3. VPN and Proxies Usage
VPN and Proxies encrypts your internet connection, shielding your online activities and personal information from eavesdroppers, especially on insecure public Wi-Fi networks.
They keep you hidden from Sybil attacks.
4. Antivirus Software
Keep your device safe with robust antivirus software. Regular scans can detect and neutralize threats that could compromise your system’s security.
5. Wallet Protective Extensions
Browser extensions dedicated to wallet protection can prevent scams and unauthorized transactions by alerting you to potential risks before you engage with them. There are several browser extensions designed for wallet protection that can help prevent scams and unauthorized transactions in the crypto space. Here are a few examples:
Rabby Wallet: In addition to being a versatile crypto wallet, Rabby offers features for managing smart contract permissions and integrates protective measures against potentially unsafe dApps, malicious websites and unauthorized transactions.
WalletGuard: This extension provides alerts if you navigate to a suspected malicious website, adding an extra layer of security against scams.
6. Revoke.cash for Permission Management
Regularly use platforms like Revoke.cash to inspect and revoke permissions you’ve granted to dApps, reducing the risk of unauthorized transactions.
7. Burner Wallets for Airdrops
Use dedicated "burner wallets" for airdrop activities. These should contain only minimal amounts of cryptocurrency and should be separate from your main wallets.
8. Webacy for Continuous Monitoring
Use services like Webacy for ongoing monitoring of your wallets. They provide instant alerts on wallet activities, enhancing your ability to respond quickly to unauthorized actions.
9. Social Media Vigilance
Exercise extreme caution with airdrop announcements on social media. Verify all information through multiple official channels and be wary of direct message scams.
Beware of Fraudulent Airdrop Emails
Never trust unsolicited emails promising airdrops. These are often phishing attempts. Legitimate airdrops will not require sensitive personal information via email. Always verify the authenticity of such offers through official websites or trusted crypto communities.
The crypto space, especially airdrop farming, is a complex and risky environment. By adopting these safety measures, you can significantly reduce the risks and safeguard your digital assets.
Here are some basic advices to avoid getting your Web3 wallet hacked:
You can use https://revoke.cash to revoke all approved contracts simply, or on Rabby wallet if you use it, there is a special section to revoke.
If you want to farm airdrops, be sure to do your due diligence before signing anything, and use a wallet address dedicated to airdrops, look at the Guide to Safe Airdrop Farming.
Always read what you sign with your wallet, never sign blind.
Again, avoid connecting your wallet to strange websites without DYOR before.
Do not click on mail received that talks about your web3 wallet (eg. metamask, trust wallet) account, or about Airdrops without DYOR before.
Do not hold more than $100 in a hot wallet, since the hot wallet's security level fully depends on your computer health in terms of security.
Finally, we fully recommend using a cold wallet like ledger to secure your funds, Ledger is fully compatible with Space Token and works fine with any web3 wallet.
Last updated